Use GitHub Actions to scan Terraform module code
Categories:
2 minute read
I wanted a way to manage my Terraform code in a better way. Checking the code for syntax errors, security vulnerabilities and producing and updating documentation. Doing this well and doing it manually is mostly impossible so I created a GitHub Action to do it for me.
Each steps is ordered in such a way that the workflow will exit with an error if problems are found which triggers a Slack message to be sent with details. This means that if bad code or security vulnerabilities are added to the repository then it will be discovered and action can taken.
The steps are order logically so we start with simple Terraform formatting to adjust the code layout as per Hashicorp best practices then move through linting, security scanning and lastly updating the README.md file with details of the Terraform module.
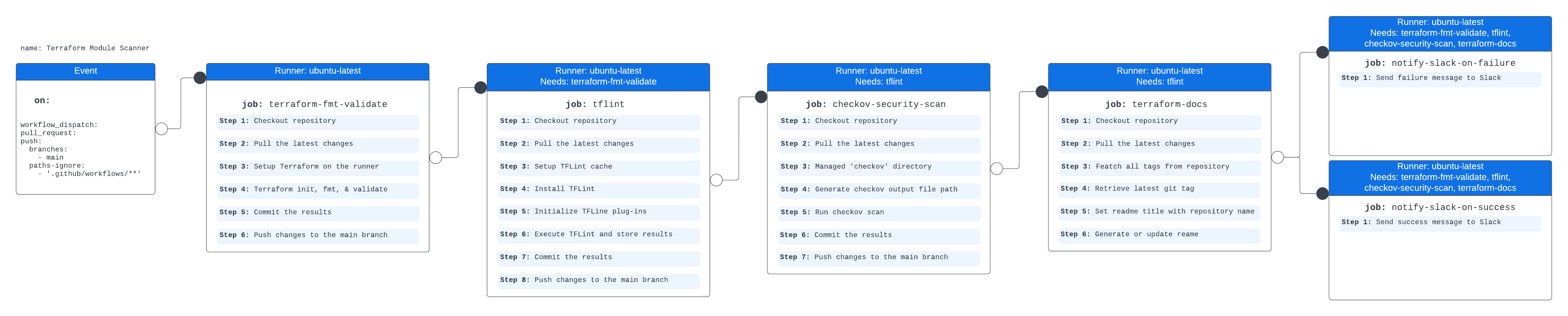
Event
This workflow is triggered by manual dispatch, pull requests, and pushes to the ‘main’ branch. However, it ignores any changes made within the ‘.github/workflows/’ directory.
Terraform FMT & Validate
Set up the Terraform environment on the runner machine and validate the Terraform code to ensure that it is ready for further deployment or management of infrastructure resources
If the terraform validate command fails, subsequent steps in the workflow will not execute.
TFLint
This workflow lints Terraform configurations using TFLint and commits the results to the repository.
Checkov Security Scan
Run a security scan on the Terraform code using the Checkov tool and commits the results to the repository.
Terraform Docs
Automatically generate and update documentation for Terraform modules in the README.md file, and push the changes back to the pull request branch in GitHub.