Azure Express Route
5 minute read
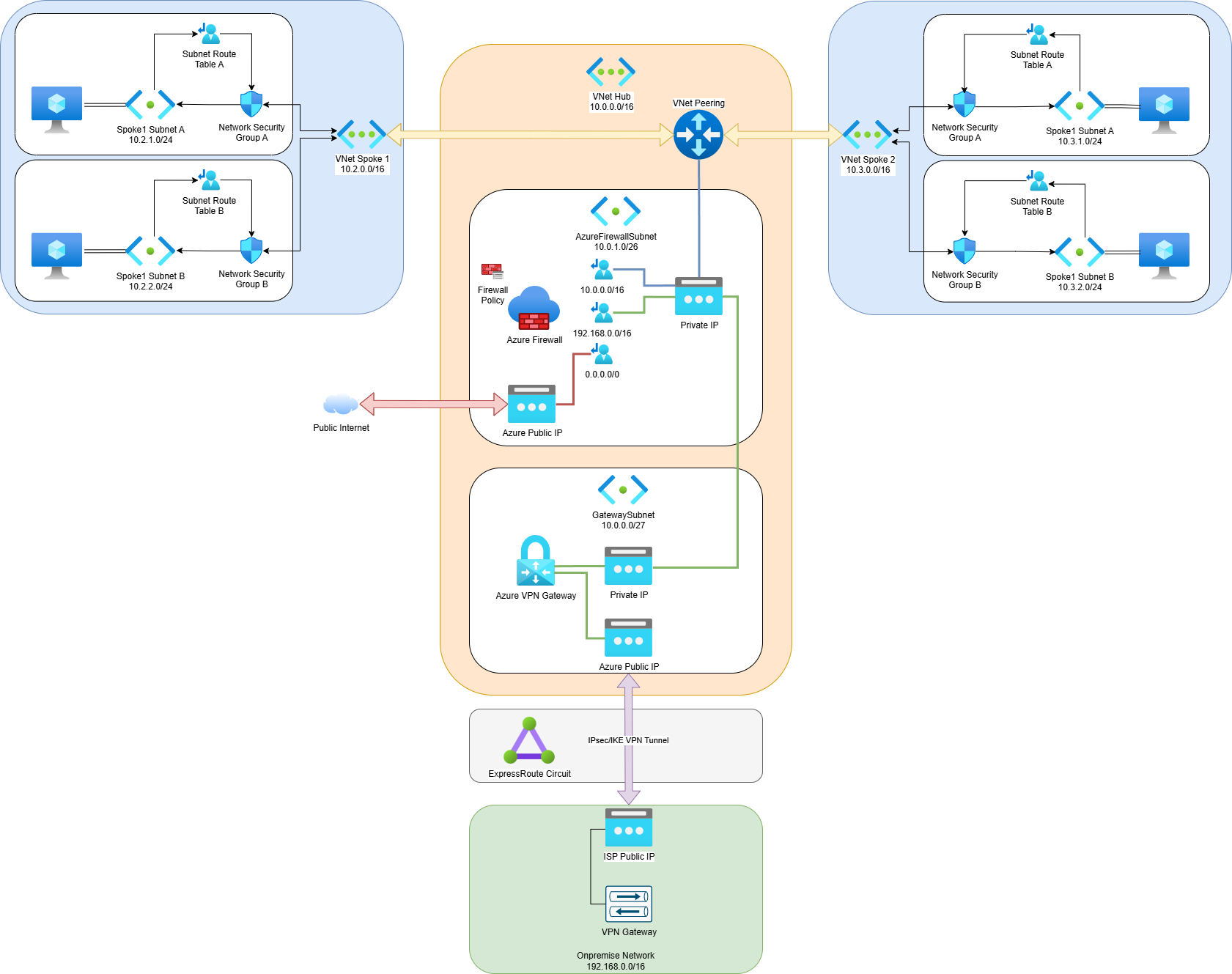
Hub and Spoke Landing Zone
The hub-and-spoke model is a popular architecture for managing and securing network traffic.
Hub VNet: This will be the central VNet that connects to the on-premises network via ExpressRoute.
Spoke VNets: These VNets will be peered with the Hub VNet. Each spoke can represent different environments or workloads.
ExpressRoute Gateway: This will be in the Hub VNet and will connect to your on-premises network.
VPN Gateway: Provides secure connectivity to on-premises networks.
Azure Firewall: Protects the network by controlling inbound and outbound traffic.
Network Security Groups (NSGs): Apply these to subnets to control inbound and outbound traffic.
Route Tables: Use custom route tables to direct traffic between VNets and the on-premises network.
VNet Address Space
- Ensure non-overlapping address spaces between the hub and spoke VNets.
- Use private IP address ranges as per RFC 1918 (e.g., 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16).
- Plan for future growth by reserving additional address space.
GatewaySubnet
The GatewaySubnet is a critical component in the hub VNet, as it hosts the resources that facilitate connectivity between your Azure environment and your on-premises network.
- Address Space: Recommended size is /27 or larger (e.g., 10.0.0.0/27).
ExpressRoute Gateway
- Provides a private, high-throughput connection between Azure and your on-premises network.
- Connects to the on-premises network via an ExpressRoute circuit. The circuit is established through a connectivity provider, which links your on-premises network to the Azure region where your VNet is located.
- Requires an ExpressRoute circuit, which includes a service key provided by the connectivity provider. The gateway is configured with the circuit’s details to establish the connection.
Unlike the VPN Gateway, which uses a public IP address to establish secure connections over the public internet, the ExpressRoute Gateway uses a private, dedicated connection provided by the ExpressRoute circuit. This circuit is established through a connectivity provider, ensuring a private and high-throughput connection between your on-premises network and Azure. It does not have a private or public IP.
VPN Gateway
- Provides secure, encrypted connectivity between Azure and your on-premises network over the public internet.
- Connects to the on-premises network via IPsec/IKE VPN tunnels. The VPN Gateway can be configured for site-to-site, point-to-site, or VNet-to-VNet connections.
- Requires a public IP address and a VPN device on the on-premises side. The VPN Gateway is configured with the on-premises VPN device’s IP address and shared key to establish the VPN tunnel.
IP addresses
Private IP The private IP address is used for communication within the VNet and for routing traffic between the hub and spoke VNets. The private IP address is automatically assigned from the address space of the GatewaySubnet.
Public IP The public IP address attached to the VPN Gateway is provided by Azure. When you create a VPN Gateway, Azure automatically assigns a public IP address to it. This public IP address is used to establish the IPsec/IKE VPN tunnels between the VPN Gateway and your on-premises VPN device.
AzureFirewallSubnet
The AzureFirewallSubnet is dedicated to hosting the Azure Firewall, which provides network security by controlling inbound and outbound traffic.
- Address Space: Recommended size is /26 or larger (e.g., 10.0.1.0/26).
Azure Firewall
The Acts as a central control point for network security, managing and monitoring traffic between subnets, VNets, and the internet.
Traffic Flow
Inbound Traffic from On-Premises Network:
- Traffic from the on-premises network enters Azure through the ExpressRoute Gateway or VPN Gateway in the GatewaySubnet.
- The traffic is routed to the AzureFirewallSubnet, where the Azure Firewall inspects and applies security rules.
- If the traffic is allowed by the firewall rules, it is forwarded to the appropriate subnet or VNet within Azure.
Outbound Traffic to On-Premises Network:
- Traffic from Azure resources (e.g., VMs in spoke VNets) is routed to the AzureFirewallSubnet.
- The Azure Firewall inspects the outbound traffic and applies security rules.
- If the traffic is allowed, it is forwarded to the GatewaySubnet, where it exits Azure through the ExpressRoute Gateway or VPN Gateway to reach the on-premises network.
East-West Traffic (Between Subnets/VNets):
- Traffic between subnets or VNets within Azure is routed to the AzureFirewallSubnet.
- The Azure Firewall inspects the traffic and applies security rules.
- If the traffic is allowed, it is forwarded to the destination subnet or VNet.
IP addresses
Private IP Address Used for internal communication within the VNet and for routing traffic between subnets and VNets. Automatically assigned from the address space of the AzureFirewallSubnet.
Public IP Address Used for outbound traffic to the internet and for managing inbound traffic from the internet. You need to create and associate a public IP address with the Azure Firewall during its deployment.
Routing Traffic
Routing in Azure involves directing network traffic between different subnets, VNets, and external networks. This is achieved using route tables and user-defined routes (UDRs).
Key Routes
Default Route (0.0.0.0/0):
- Next Hop: Azure Firewall private IP address.
- Purpose: Directs all outbound internet traffic through the Azure Firewall.
On-Premises Route:
- Address Prefix: On-premises network address space (e.g., 10.1.0.0/16).
- Next Hop: Virtual network gateway (ExpressRoute Gateway or VPN Gateway).
- Purpose: Directs traffic destined for the on-premises network through the appropriate gateway.
VNet Peering Route:
- Address Prefix: Address space of peered VNets.
- Next Hop: Virtual network peering.
- Purpose: Directs traffic between peered VNets.
Feedback
Was this page helpful?
Glad to hear it!
Sorry to hear that.